Global Protect Components
Certificate Management
Connections
Authentication
Debugging
Tech Content Creator DISCLAIMER: This is my private professional blog -my engineering raw notes supporting Palo Alto Environment. I've been working with Security products for more than 40+ years. Everything expressed in this blog is my own opinion and not those of Palo Alto. - Om JaiSaiRam
menu
- Mod 1. Security Platform and Architecture
- Mod 2:Configuring Initial Firewall Settings
- Mod 3: Managing Firewall Configurations
- Mod 4: Managing Firewall Administrator Accounts
- Mod 5: Connecting the Firewall to Production Networks with Security Zones
- Mod 6: Creating & Managing Security Policy Rules
- Mod 7: Creating & Managing NAT Policy
- Mod 8: Controlling Application Usage with App-ID
- Mod 9: Blocking Known Threats using Security Profiles
- Mod 10. Blocking Inappropriate Web Traffic with URL Filtering
- Mod 11: Blocking Unknown Threats with WildFire
- Mod 12. Controlling Access to Network Resources with User-ID
Monday, December 15, 2025
Global Protect Troubleshooting
Tuesday, November 11, 2025
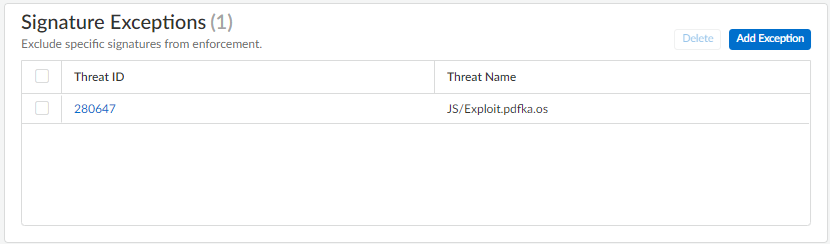
Threat ID Vulnerability profile override (exception)
Palo Alto Networks defines a recommended default action (such as block or alert) for threat signatures. You can use a threat ID to exclude a threat signature from enforcement or modify the action that is enforced for that threat signature. For example, you can modify the action for threat signatures that are triggering false positives on your network.
Configure threat exceptions for antivirus, vulnerability, spyware, and DNS signatures to change enforcement for a threat. However, before you begin, make sure the threats are being properly detected and enforced based on the default or best practice signature settings for an optimum security posture:
Get the latest Antivirus, Threats and Applications, and WildFire signature updates (for the firewall).
Set Up Antivirus, Anti-Spyware, and Vulnerability Protection and apply these security profiles to your security policy.
For SCM, adding or updating a Vulnerability profile override (exception) has to be done in the Overrides section. We are all used to editing the profile and making the change in the exceptions tab, but as we saw you can’t do that in SCM.
- To add an override, click Add Override
- Search for the Threat ID or Name
- Check the box to select the Threat
- Change the Action to Allow
- Click + to add the IP address
- Check the box to select which profile to want to add it to
- Save
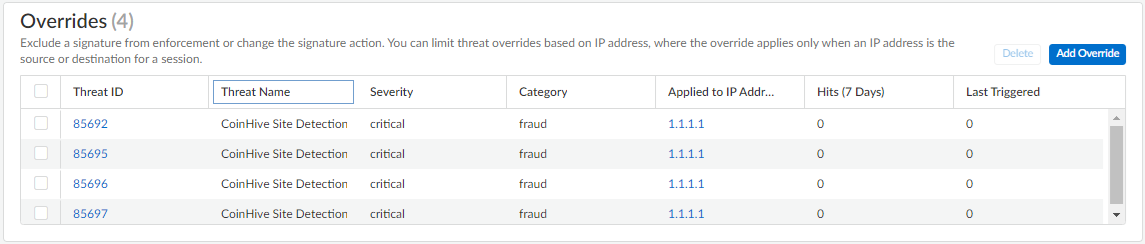
To update an override, in the
Overrides section, click on the Threat ID
- Click on the name of the Profile
- Click + to add an IP address or – to delete one
- Save the update
- Save the override of the Threat ID
Strata Cloud Manager

- Repeat to add additional exceptions or click Save after all of your threat exceptions have been added.
- Modify enforcement for vulnerability and spyware signatures (except DNS signatures; while they are a type of spyware signature, DNS signatures are handled through the DNS Security subscription in Prisma Access).
- Select ConfigurationNGFW and Prisma AccessSecurity ServicesAnti-Spyware or ConfigurationNGFW and Prisma AccessSecurity ServicesVulnerability Protection, depending upon the signature type.
- Add Profile or select an existing Anti-Spyware or Vulnerability Protection profile from which you want to modify the signature enforcement, and then select Add Override.
- Search for spyware or vulnerability signatures by providing the relevant Match Criteria. This automatically filters the available signatures and displays the results in the Matching Signatures section.
- Select the check box for the signature(s) whose enforcement you want to modify.
- Provide the updated Action, Packet Capture, and IP Addresses that you want the modified enforcement rules to apply to for the selected signatures.
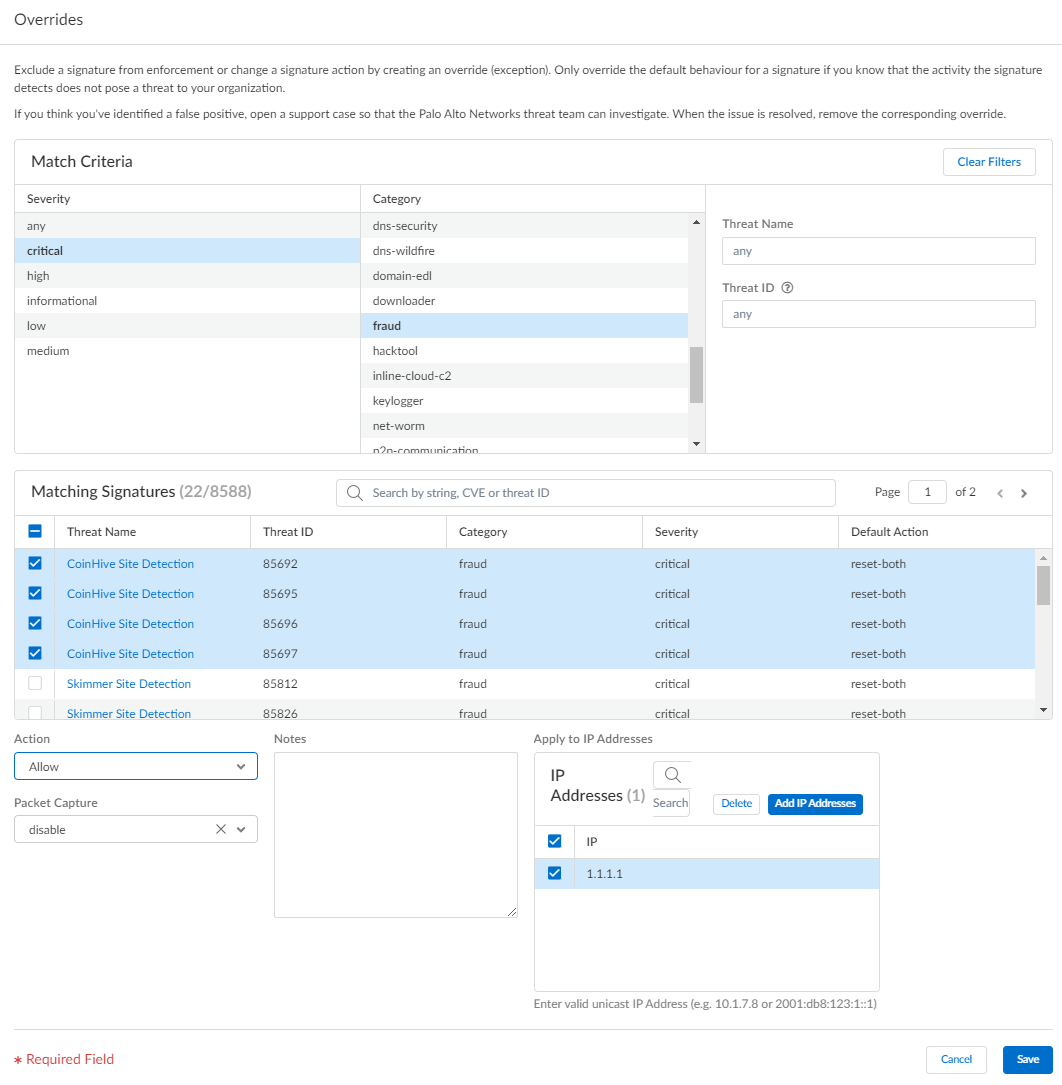
- Save your updated signature enforcement configuration.
- You can view a complete list of Overrides including various statistics, as well as Delete entries that are no longer necessary.
Wednesday, November 5, 2025
How to Setup a Site to Site Tunnel
Build Site to Site tunnel
Service Connections Setup
Verify Service Connection Status
- IKE Crypto Profile (Phase 1)
- IPSec Crypto Profile (Phase 2)
- IKE Gateway (Phase 1)
- Zones
- Tunnel Interface
- IPSec Tunnel (Phase 2)
- Virtual Router
- Static Routes
- Security Policy
You create IKE-Crypto-Profile, IPSec-Crypto-Profile
IKE Gateway (use the IKE-Crypto-Profile)
IPSec Tunnel (use IKE Gateway and IPSec-Crypto-Profile)
IKE Crypto Profile (IKE Phase 1)
Name: pa-lab-ike-crypto-profile
DH Group: Group20
Authentication: non-auth
Encryption: aes-256-gcm
Timers: 1 Hour
IPSec Crypto Profile (IKE Phase 2)
Name: pa-lab-IPSec-crypto-profile
ESP - Encapsulating Security Payload
AH - Authentication Header
Encryption: aes-256-gcm
Authentication: sha256
DH Group: Group
Life Time: 1 Hour
IKE Gateway
Name: pa-lab-service-connection-IKE-gateway
Version: IKEv2 only Mode
Address Type: IPv4
Interface: Ethernet1/2
Local IP Address 172.16.17.1/24
Peer IP address Type: IP
Peer IP address: 203.1.113.1
Pre-shared Key: PaloAlto!
Confirm Pre-shared Key: PaloAlto!
Local Identification: User FQDN (Email address) Site-a@prisma-access.lab
Advance Tab
Enable NAT Traversal
IKE Crypto Profile: pa-lab-ike-crypto-profile
Initial Configuration
Initial Access to the System
Configuration Management
Licensing and Software Updates
Account Administration
Account Administration using Radius
Admin Roles
Interface Configuration
Security Zones
Layer 2, Layer 3, Virtual Wire, and Tap
Sub-Interface
DHCP
Virutal Routers
Multi VR Setup and Use Case
Security and NAT Policies
Security Policy Configuration
Policy Administration
NAT (Source and Destination
App-ID
App-ID Overview
Application Groups and Filters
Content-ID Overview
AntiVirus
Anti-Spyware
Vulnerability
URL Filtering
External Dynamic List
File Blocking Wildfire
Security Profiles File Blocking
WildFire
Zone Protection and DOS Protection
Decryption
Certificate Management
SSL Handshake
Outbound SSL Decryption
Inbound SSL Decryption
VPN Virtual Private Network
Allow a secure communication over public Network.
VPN try to maintain CIA (Confidentiality, Integrity and Authentication)
Types of VPN
1. Site to Site VPN (IPSec s2s)
2. Remote Access VPN ( SSL VPN or Global Protect)
IPSec Site to Site VPN requires CIA
Confidentiality: Encryption
Integrity: HASH
Authentication: PSA/PKI
It will also provide Antireplay protection
Encryption: IT will convert Plain text in to cipher text by using the key.
Decryption: It will convert Cipher Text into the plan text by using the key
Symmetric Encryption
1. DES (56 bit) 3DES (168 bit) ASE (128, 192. 256 bit) RC4 (128bit_
2. Same key used for encryption and decryption
3. Block Cipher ( DES, 3DES, block the data ex 64 bit block, ASE - Same data block whatever size of Key)
4. Stream Cipher: (RC4: Bit by Bit Encryption)
Asymmetric Encryption
1. RSA (SSH), DH
2. Both sites have 2 keys Private and Public key. Share public key with each other
When ever data is encrypted with private key, you can use public key to decrypt it and visa versa
HQ Head Office in Delhi
Branch Office BLR Bangalore
Global Protect Troubleshooting
Global Protect Components Certificate Management Connections Authentication Debugging https://www.youtube.com/watch?v=0Z48WHvyW0Q authentica...

-
Module 6: Creating and Managing Security Policy Rules Day 2 \ checkpoint firewall N...
-
PAN-OS CLI Commands show chassis inventory show netstat route yes show transceiver all show system info show system info | match serial sh...
-
Module 2 Palo Alto Initial Configuraiton Initial Configuration Administrative controls Initial Access to the system Configuration mana...


























































